Protect My Assets
Threats
Why You Need Protect My Assets - Threats
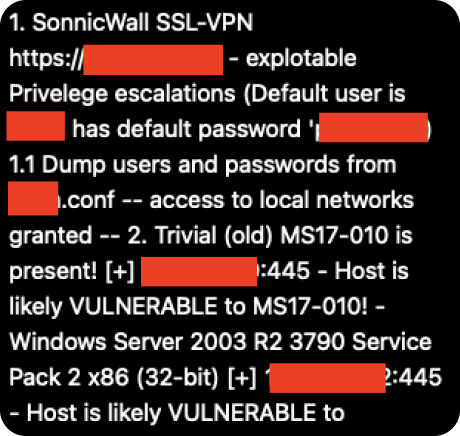
Firewalls and perimeter defenses are important — but they’re not enough. Cyber attackers are getting smarter. They use phishing emails, fake websites, and hidden vulnerabilities to sneak past traditional security tools.
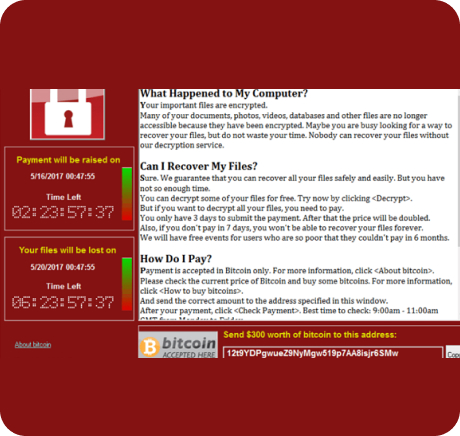
And once they’re in, they can move through your network undetected, stealing data or planting malware.
That’s where Protect My Assets – Threats comes in.
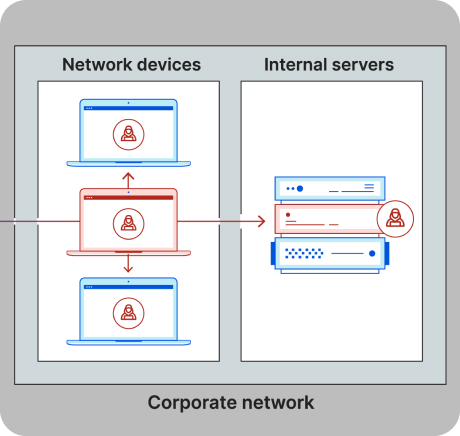
Instead of sitting at the edge of your network like a firewall, PMY-Threats works inside your network. It watches for unusual activity, alerts you to intrusions, and helps stop attackers before they cause damage.
Invest today. Protect tomorrow.
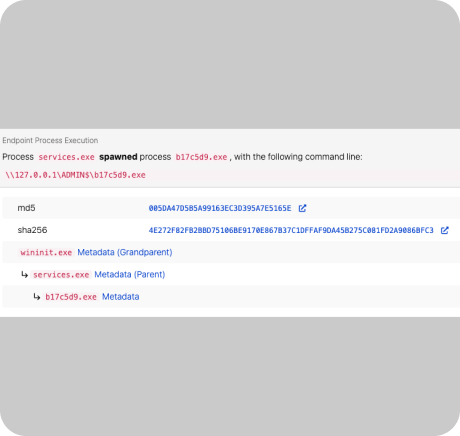
Internal threats and lateral movement
Once inside, intruders can remain undetected for weeks or even months — quietly moving from system to system, escalating privileges, and exfiltrating sensitive data. This gap between perimeter defense and actual detection is where organizations are most vulnerable.
Protect My Assets – Threats is designed to close that gap.
PMY – Threats sits inside your network, continuously analyzing behavior, detecting anomalies, and alerting you to signs of compromise even those engineered to evade conventional detection.